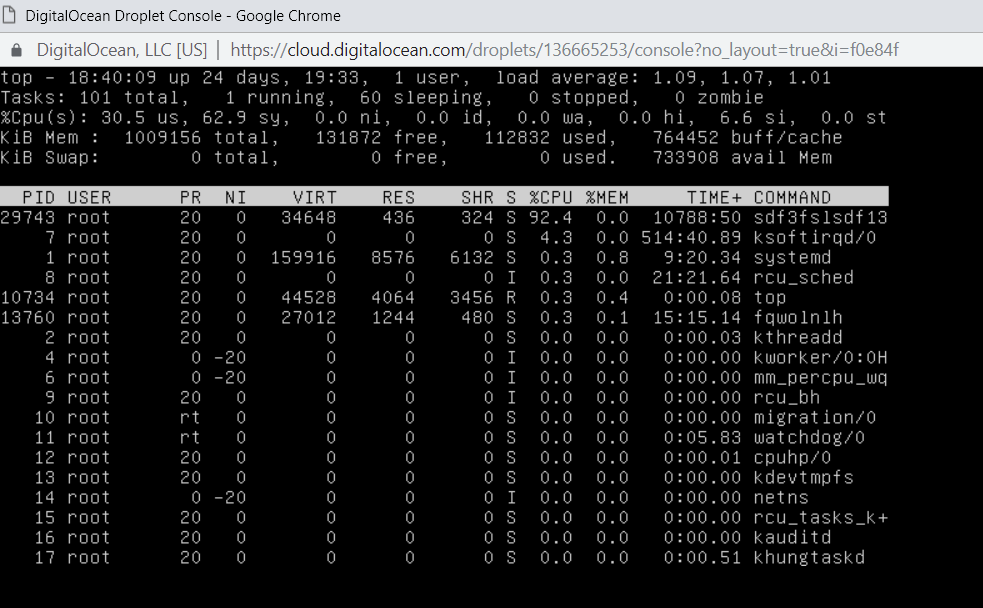
In the past months I was working on security incidents involving Linux systems and I struggled to find good material on that topic to structure well my response plan. In fact, Linux is the investigator’s black hole, blind spot, deficiency, weakness and so on.